| ||||||||||||||||
Introduction
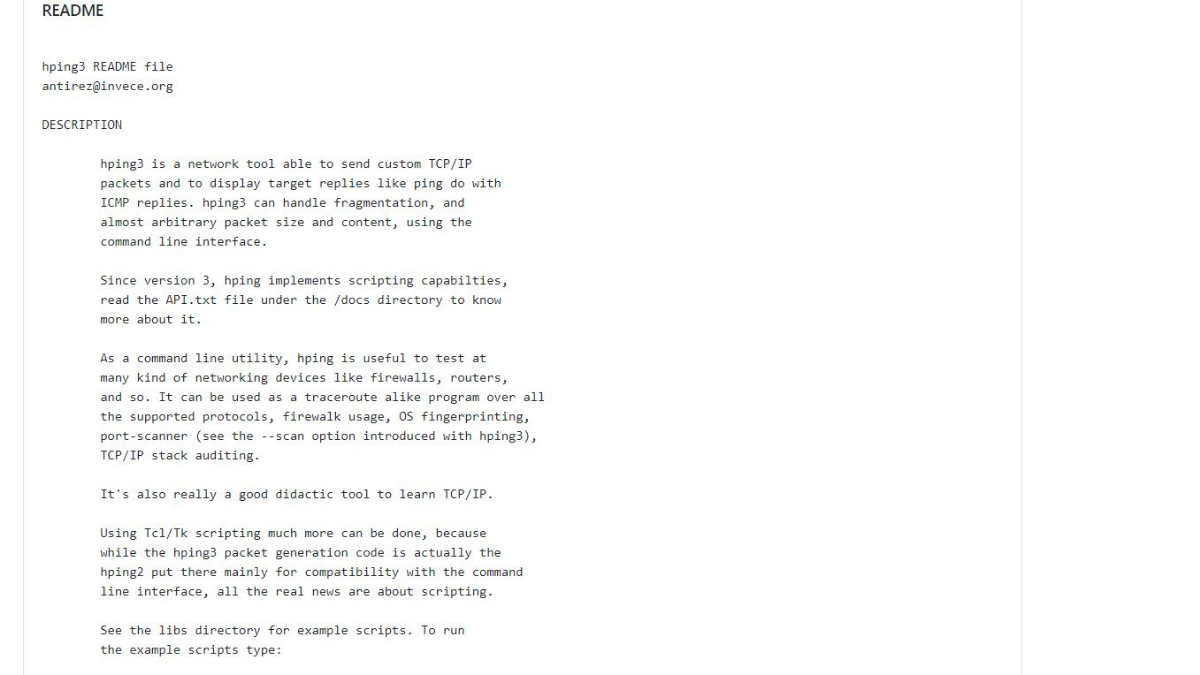
The tool hping3 allows you to send manipulated packets. This tool allows you to control the size, quantity and fragmentation of packets in order to overload the target and bypass or attack firewalls. Hping3 can be useful for security or capability testing purposes, using it you can test firewalls effectivity and if a server can handle a big. Free online tool to ping an IPv4 address or host name. The Ping utility is an online, free tool that help you to verify if a domain/server is operating and network accessible. This Ping tool uses the Internet Control Message Protocol (ICMP) Echo function as detailed in RFC 792. A small packet will be sent through the network to a given IP. Hping is often considered a complementary tool to Nmap. The tool runs on all major operating systems including Linux,.BSD, and Windows. Hping was mainly used as a security tool in the past, but now can be used in many ways to test networks and hosts. Below are the things you can do using hping: Firewall testing; Advanced Port Scanning.
Nping is an open source tool for network packet generation, responseanalysis and response time measurement. Nping can generate networkpackets for a wide range of protocols, allowing users full control over protocol headers. While Nping can be used as a simple pingutility to detect active hosts, it can also be used as a raw packet generatorfor network stack stress testing, ARP poisoning, Denial of Service attacks,route tracing, etc. Nping's novel echo mode lets users see how packets change in transit between the source and destination hosts. That's a great way to understand firewall rules, detect packet corruption, and more.
Nping has a very flexible and powerful command-line interface that grantsusers full control over generated packets. Nping's features include:
- Custom TCP, UDP, ICMP and ARP packet generation.
- Support for multiple target host specification.
- Support for multiple target port specification.
- Unprivileged modes for non-root users.
- Echo mode for advanced troubleshooting and discovery.
- Support for Ethernet frame generation.
- Support for IPv6 (currently experimental).
- Runs on Linux, Mac OS and MS Windows.
- Route tracing capabilities.
- Highly customizable.
- Free and open-source.
Downloading and Installing Nping
Download Nping for Windows, Linux, or Mac OS X as part of Nmap from the Nmapdownload page. Source code can be downloaded there as well.
For the very latest code, checkout Nmap from our SVN repository (Nping-specific code is in the nping subdirectory) as described here. Use the normal steps to compile Nmap and Nping will be compiled along with it.
Patches, Bug Reports, Questions, Suggestions, etc
Questions, comments and bug reports are always welcome. Please use the Nmapdevelopment mailing list (nmap-dev). To subscribe, please visit:http://nmap.org/mailman/listinfo/dev.
Code patches to fix bugs are even better than bug reports. If you wish tocontribute code to Nping, we have a todo list of features we would like to have.There are also some instructions forcreating patch files and sending them, here.
For contact information, please visit section 'Authors' in the man page .
Nmap Site Navigation
| Intro | Reference Guide | Book | Install Guide |
| Download | Changelog | Zenmap GUI | Docs |
| Bug Reports | OS Detection | Propaganda | Related Projects |
| In the Movies | In the News | ||
Greeting Everyone ! Hope Everything Is Going good Today we are Going to see on One Of best tool hping3 which we can define As TCP/IP packet forging tool with embedded Tcl scripting functionality . Why hping3 Important , Usage Of hping3 Let’s Discuss.
What is hping3?
hping3 is a command-line oriented TCP/IP packet assembler/analyzer. It supports TCP, UDP, ICMP and RAW-IP protocols, has a traceroute mode, the ability to send files between a covered channel, and many other features. We can Easily Verify Network traffic strange Some of Important Features Of hping3 As Below :
- Advanced port scanning
- Network testing, using different protocols, TOS, fragmentation
- Manual path MTU discovery
- Advanced traceroute, under all the supported protocols
- Remote OS fingerprinting
- Remote uptime guessing
- TCP/IP stacks auditing
- hping can also be useful to students that are learning TCP/IP.
How To setup hping3?
If Your Linux User Which Default In Various Linux Distribution Such as Kali Linux , parrot etc . As You Can See Instruction Of Installation If You have not default Visit Official Page Source: .
And You Can Follow Below Command For Installation Process:
→ sudo apt-get install hping3

Usage Of hping3:

Port Scanning Using hping3:
TCP SYN Scan To Perform classic TCP SYN Scan Against target Here We Will Use command:
→ hping3 -S IP -p 80 -c 3
As above We Used -S For SYN Scan We define -c 3 flag in order to send the SYN packet only 3. As Result:
As we scan port 80 on Traget. As we can see from the output returned packet from Target contains SYN and ACK flags set which indicates an open port As Which send Packet 3 time Based our supply value -c3 .

Perform TCP ACK Scan :
TCP ACK Scan can be performed by setting ACK flag in probe packets. To Perform TCP ACK Scan Against Our Target Here We will use Command:
→ hping3 -A 72.14.207.99 -p 80 -c 2
Siping Tool Kali
As above We Used -A For ACK Scan We define -c 2 flag in order to send the SYN packet only 2 time. As Result:
As we scan port 80 on Traget. As we can see from the output returned packet from Target contains ACK flags set which indicates an open port As Which send Packet 32time Based our supply value -c2.
UDPScans:
Siping Tool For Tires
hping3 Perform UDP Scan Against target configured to operate in UDP mode by specifying -2 the command line. Here We will Use Command:
→ hping3-2 IP -p 80 -c 1
We can also run hping3 in interactive mode My typing Command: → hping3 . As Result:
As Response We found unreachable That Mean Can not communicate With Port 80 On Our target .
ICMP Ping
To Scan Against ICMP Ping Here We will use command:
→ hping3 -1 132.148.4.168
AsWe can Also set TimestampForOur Request Here We will add -c 2 That We have set 2 Timestamp
→ hping3 -1 132.148.4.168 -c 2
Hping Security Tool
OS Fingerprinting
To Perform OS Fingerprint Against Target Which help to collect ISNs and determine their increments. Here We Will Use to Perform OS Fingerprint -Q or— seqnum
Command We Will Use: hping3 132.148.4.168 -Q -p 139 -S
As We Define -p As 139 Port We define -Q For performing OS Fingerprint Against Target.
Push and URG Scan :
Here by adding argument -F -P and -U we are setting for FIN, PUSH, And URG packet in the prob packets. Here if the port 80 is closed hping3 returns an RST Response
Here We Will Use Command: hping3 -F -P -u IP -p 80
As We scan or urgent On Port 80 Due To port Is open So here it will not give us any output. As We Used -F For FIN -P PUSH -u Urgent.
Conclusion: So Today we Discussed Basic About hping3 which Important tool For scan Networks against Target As we Discussed How We can Implement Our Testing phase Using hping3 . We Discuss TCP SYN Scan, TCP ACK Scan, UDP Scan etc. Hope Cleared Basic usage Of hping3 . Bye !
For More : https//securiumsolutions.com/blog