It includes a complete hypervisor, based on xhyve/bhyve, which is optimized for lightweight virtual machines and container deployment. It is designed to be interfaced with higher-level components such as the VPNKit and DataKit. HyperKit currently only supports macOS using the Hypervisor.framework. It is a core component of Docker Desktop for Mac. Docker support for Citrix Hypervisor is a feature of Citrix Hypervisor 6.5 SP1 and can be downloaded from the Citrix Hypervisor download page. The support is delivered as a supplimental pack named 'xs-container' which also includes support for CoreOS and cloud-drives.
Does Docker Need Hardware Virtualization?
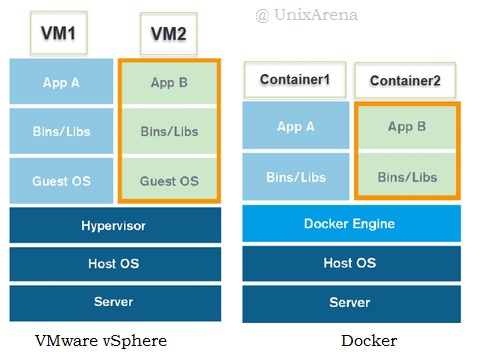
Docker
Samsung easy printer manager descargar mac. This is a quick post to explain that by default Docker does not need hardware virtualization (VT-X).
Is Docker a Virtualization?
In a sense of allowing you to run multiple independent environments on the same physical host, yes. Docker containers allow you to run processes in isolation from each other and from the base OS – you decide and specify if you want base system to share any resources (IP addresses, TCP ports, directories with files) with any of the containers.
The key difference from KVM or VMware virtualization is that Docker is not using hardware virtualization. Instead, it leverages Linux functionality: namespaces and control groups.
Linux namespaces are provided and supported by Linux kernel to allow separation (virtualization) of process ID space (PID numbers), network interfaces, interprocess communication (IPC), mount points and kernel information.
Control groups in Linux allow accurate resource control: using control groups allows Docker to limit CPU or memory usage for each container.
Does Docker use Hardware Virtualization?
The short answer is: no. Docker needs a 64-bit Linux OS running a modern enough kernel to operate properly. Which means if that what you have happily running on your hardware without hw virtualization support, it will be plenty enough for Docker.
Now, this gets a bit tricky when you’re talking about Docker in Windows or MacOS. They don’t have a native Linux environment, so they have to run a Linux virtual machine that runs the Docker engine. Bamini tamil font online, free download. You then typically have command line tools installed in your base OS (Windows or MacOS) that allow seamless management of the Docker containers in the Docker VM.
Does Your CPU Support Hardware Virtualization?

You can grep the special /proc/cpuinfo file for a quick answer:
if it contains vmx – you have an Intel CPU and it supports HW virtualizationif it contains svm – you have an AMD CPU and it supports HW virtualizationHere’s how this looks on my XPS laptop:
cat /proc/cpuinfo on Dell XPS laptop
See Also
- Docker Storage Volumes Clean-up
Windows containers offer two distinct modes of runtime isolation: process and Hyper-V isolation. Containers running under both isolation modes are created, managed, and function identically. They also produce and consume the same container images. The difference between the isolation modes is to what degree of isolation is created between the container, the host operating system, and all of the other containers running on that host.
Process Isolation
This is the 'traditional' isolation mode for containers and is what is described in the Windows containers overview. With process isolation, multiple container instances run concurrently on a given host with isolation provided through namespace, resource control, and process isolation technologies. When running in this mode, containers share the same kernel with the host as well as each other. This is approximately the same as how Linux containers run.
Hyper-V isolation
This isolation mode offers enhanced security and broader compatibility between host and container versions. With Hyper-V isolation, multiple container instances run concurrently on a host; however, each container runs inside of a highly optimized virtual machine and effectively gets its own kernel. The presence of the virtual machine provides hardware-level isolation between each container as well as the container host.
Isolation examples
Create container
Managing Hyper-V-isolated containers with Docker is nearly identical to managing process-isolated containers. To create a container with Hyper-V isolation using Docker, use the --isolation parameter to set --isolation=hyperv.
To create a container with process isolation through Docker, use the --isolation parameter to set --isolation=process.
Citrix Hypervisor With Docker - Citrix
Windows containers running on Windows Server default to running with process isolation. Windows containers running on Windows 10 Pro and Enterprise default to running with Hyper-V isolation. Starting with the Windows 10 October 2018 update, users running a Windows 10 Pro or Enterprise host can run a Windows container with process isolation. Users must must directly request process isolation by using the --isolation=process flag.
Warning
Running with process isolation on Windows 10 Pro and Enterprise is meant for development/testing. Your host must be running Windows 10 build 17763+ and you must have a Docker version with Engine 18.09 or newer.
You should continue to use Windows Server as the host for production deployments. By using this feature on Windows 10 Pro and Enterprise, you must also ensure that your host and container version tags match, otherwise the container may fail to start or exhibit undefined behavior.
Isolation explanation
This example demonstrates the differences in isolation capabilities between process and Hyper-V isolation.
Here, a process-isolated container is being deployed and will be hosting a long-running ping process. Ableton 10 keygen v1 3 0 mac.

Using the docker top command, the ping process is returned as seen inside the container. The process in this example has an ID of 3964.
On the container host, the get-process command can be used to return any running ping processes from the host. In this example there is one, and the process id matches that from the container. It is the same process visible from both container and host.
To contrast, this example starts a Hyper-V -solated container with a ping process as well.
See Full List On Etherealmind.com
Likewise, docker top can be used to return the running processes from the container.
However, when searching for the process on the container host, a ping process is not found and an error is thrown.
Docker Container Hypervisor
Finally, on the host, the vmwp process is visible, which is the running virtual machine that is encapsulating the running container and protecting the running processes from the host operating system.